Black Hole Attack Implementation in Ns2
How to implement black hole attack using ns2 codeWhat is black hole attack:
A black hole has two properties.
- First is the node exploits the ad hoc routing protocol, such as AODV protocol , to advertise itself as having a valid route to a destination node. Node which exploits AODV Protocol route is spurious, which has intention to make intercepting packets.
- Second, The Node Which exploits AODV Protocol route consumes the intercepted packets.
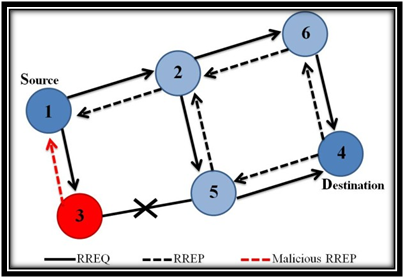
Classification black hole attack:
Black hole Attack can be classified into following types,
- Passive black hole attack in ns2 .
- Active black hole attack in ns2.
- Common black hole attack in ns2.
Models of black hole attacks in ns2 :
- Active black hole node receives the RREQ packet and returns false RREP packet.
- Active black hole node receives RRER or RREP packets and process them normally.
- Active black hole node receives a data packet and discards it.
- Passive black hole node receives a data packet and discards it.
- Passive black hole node receives an AODV routing packet and normally process it.
- Ordinary black hole node discards all packets.
NS2 Projects Video Output
See our Latest Video Output of Ns2 Projects on Various Domain.
Ns2 Projects
Customized NS2 Projects for B.E/B.Tech/M.E/M.Tech/Ms/PhD Scholars.
Ns2 Projects Screen Shots
Ns2 Projects Screen Shots.Regular Update of NS2 Projects Screenshots here!
Sample code for black hole attack:
#Code that defines black hole attackers in ns2 simulation:
nsaddr_t malicious1;
nsaddr_t malicious2;
nsaddr_t malicious3;
#code for initializing black hole attackers:
int
AODV::command(intargc, const char*const* argv) {
if(argc == 2) {
Tcl&tcl = Tcl::instance();
if(strncasecmp(argv[1], "id", 2) == 0) {
tcl.resultf("%d", index);
return TCL_OK;
}
if(strcmp(argv[1], "blackhole1") == 0) {
malicious1= index;
printf("malicious %d", malicious1);
return TCL_OK;
}
if(strcmp(argv[1], "blackhole2") == 0) {
malicious2=index;
printf("malicious %d", malicious2);
return TCL_OK;
}
if(strcmp(argv[1], "blackhole3") == 0) {
malicious3= index;
printf("malicious %d", malicious3);
return TCL_OK;
}
AODV::AODV(nsaddr_t id) : Agent(PT_AODV),
btimer(this), htimer(this), ntimer(this),
rtimer(this), lrtimer(this), rqueue() {
index = id;
seqno = 2;
bid = 1;
LIST_INIT(&nbhead);
LIST_INIT(&bihead);
malicious1=999;
malicious2=999;
malicious3=999;a
Journal Support for Research Scholars

Ns2 Projects Work Progress
- MANET – Mobile Ad Hoc Network 95%
- VANET – Vechicle Ad Hoc Netwok 97%
- LTE – Long Term Evolution 78%
- IoT – Internet of Things 90%
- Wireless Sensor Network 89%
- Network Security 89%
- Ns2 Attacks 96%
- Cognitive Radio Network 85%
- Parallel and Distributed Computing 73%
- SDN – Software Defined Networking 95%
- P2P , Video Streaming , Peersim 96%
- IPV4 , IPV6 88%
- 4G Network , 5G Network 80%
- Visual , Underwater Sensor Network 79%
- Multicasting Communication 84%
- Wimax, WiFi 90%
- OFDMA 94%
Our Achievements – Ns2 Projects

